A couple of days ago, I analyzed a piece of malware widespread on "The Pirate Bay" torrent tracker. I'm documenting my findings in this article.
Quick note: I don't condone piracy. This article is for research and educational purposes. No pirated material was involved in the making.
First off, if you don't already know, "The Pirate Bay" (abbreviated TPB) is one of the biggest public torrent trackers online. And "thepiratebay.org" (one of its main domains) has a Global rank of 215 on Alexa at the time of this writing (and 135 in the US ?).
.
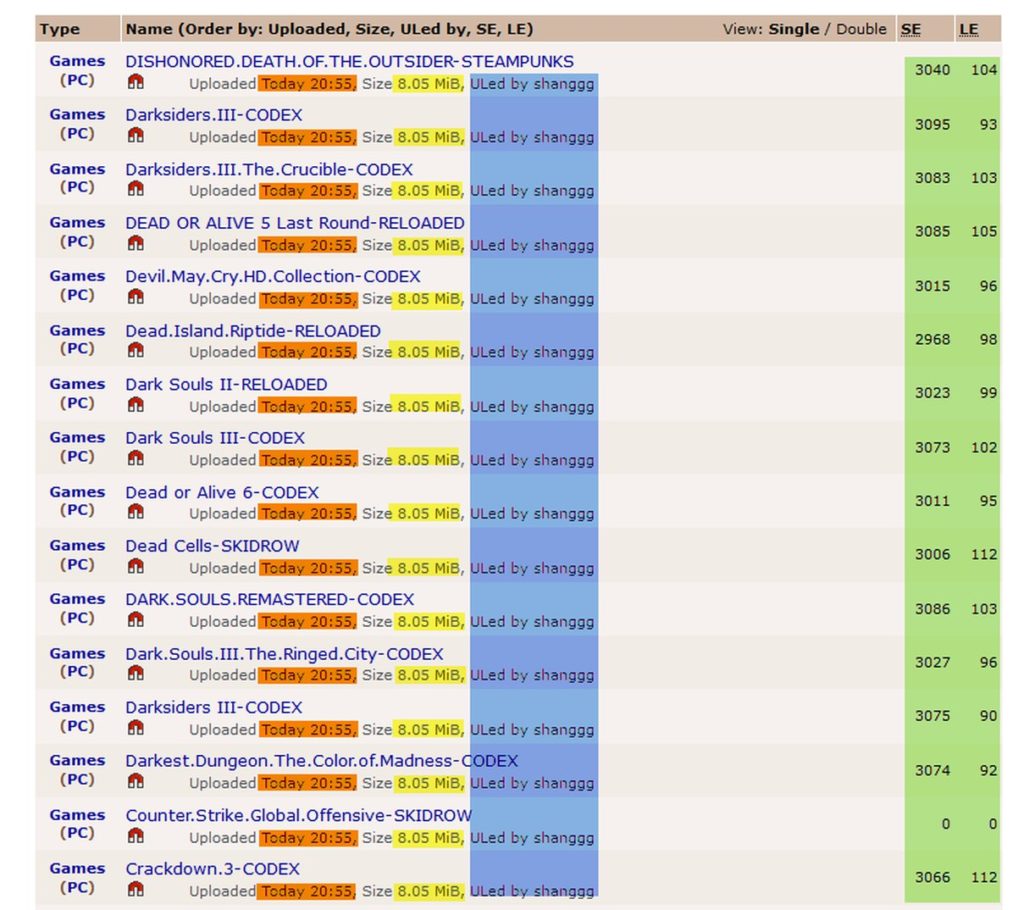
If we navigate to that website, and check the latest PC games, we'll find something like this:
We note that all the files:
- Were uploaded on the same time (highlighted in orange).
- Are of the same filesize; 8.05 MB (highlighted in yellow).
- Were uploaded by the same account (highlighted in blue).
- Have a big random number of seeders and leechers; which is fake of course (highlighted in green).
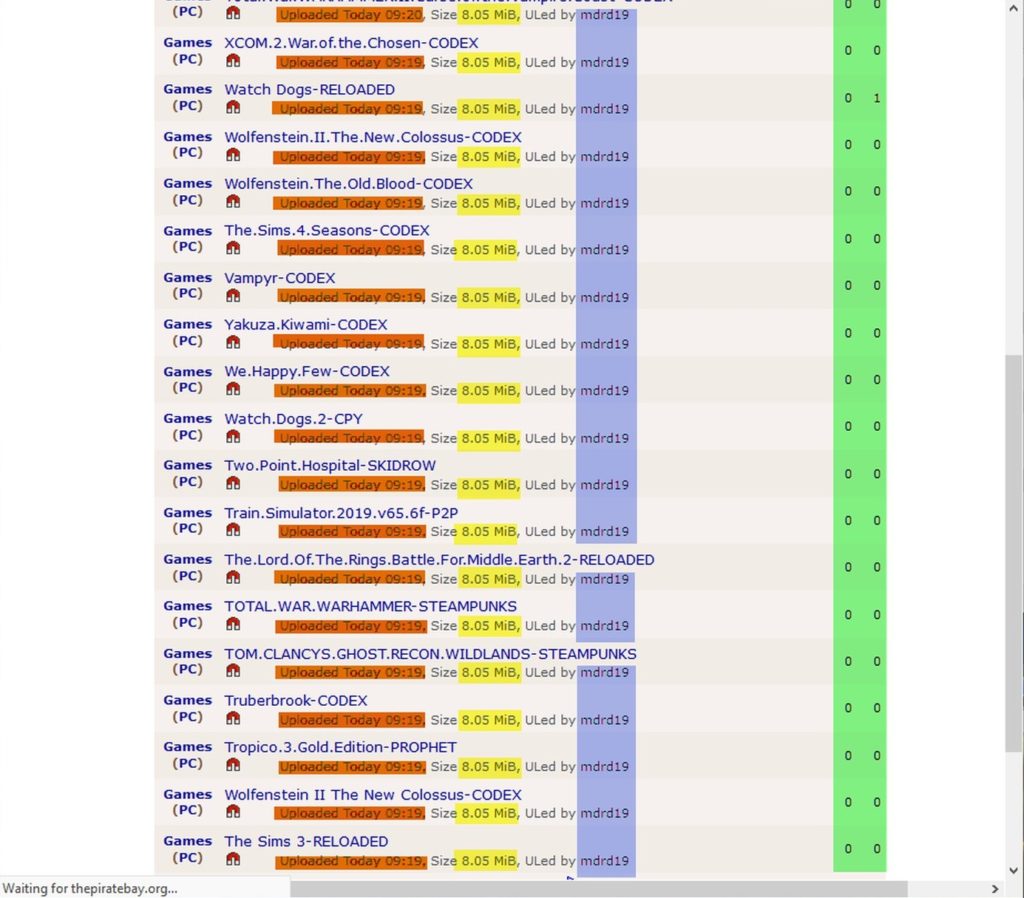
A couple of days later, I found a similar list, but uploaded from a different account
This happens every day, until the torrents are removed by a moderator or something.
So, lets download some samples and examine them..
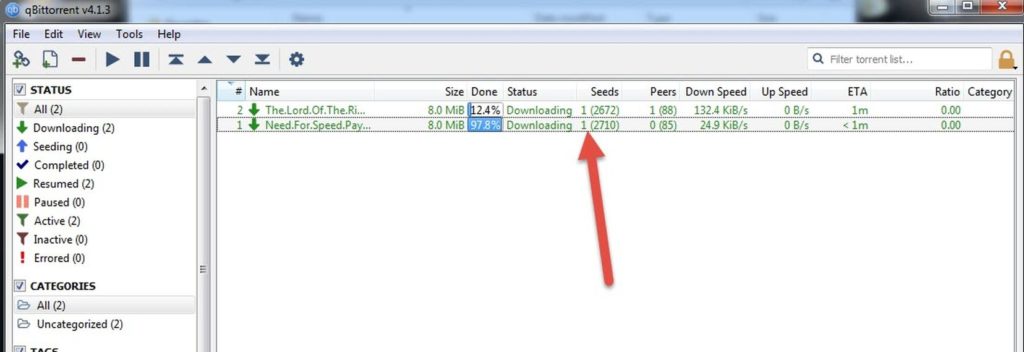
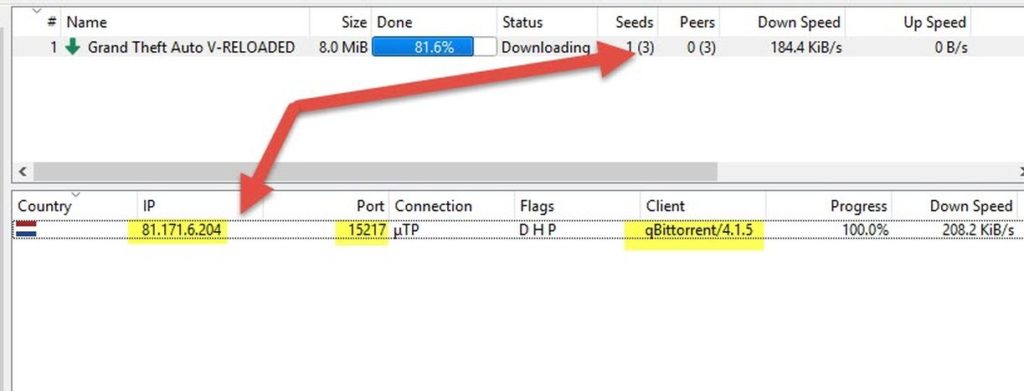
I downloaded those 3 samples at different times on different machines. The first thing I noticed is that, every time there was only 1 actual seeder (despite the swarm showing thousands). qBittorrent shows us that this seeder has the IP 81.171.6.204 (in Netherlands) and is using "qBittorrent 4.1.5" . Most probably this machine belongs to our malware's author (or one of his seedboxes or zombies).
This is what we get after downloading:
- setup.zip
- keys.nfo
The ".nfo" file is non-executable, so it won't be of concern here.
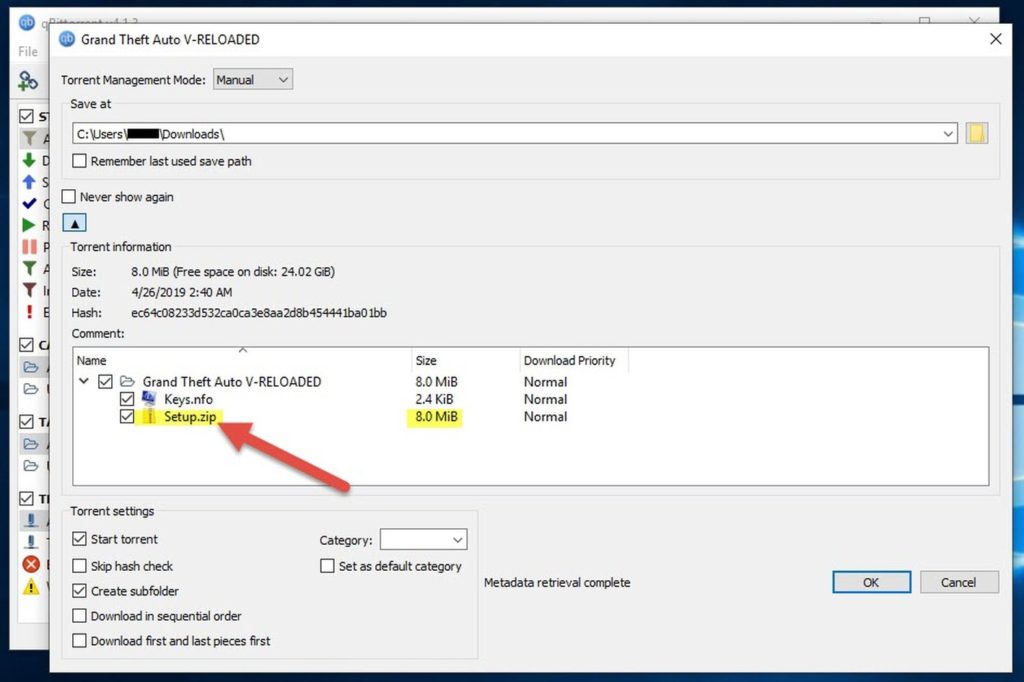
Lets see what's inside "setup.zip"
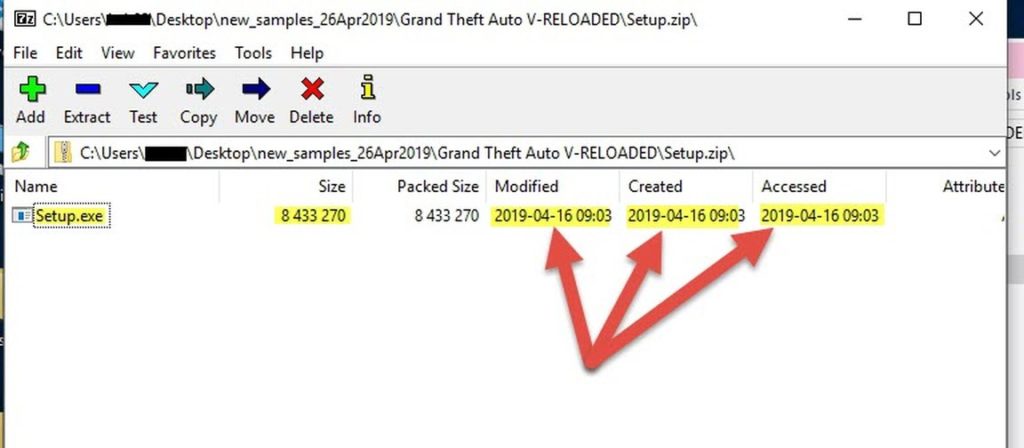
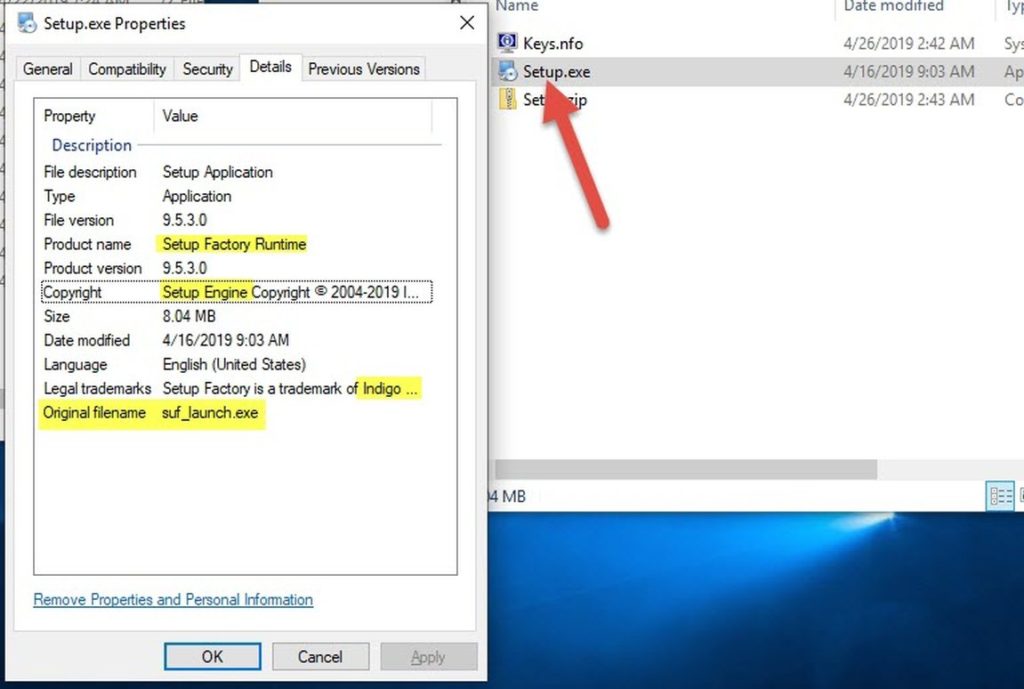
A single "setup.exe" file. This is our main malware. Its metadata show us that its creation date is 16-Apr-2019. Plus some valuable info..
The original filename was "suf_launch.exe", and it has other properties too (Product name, Product version, Copyright) that lead us to believe that this executable is an installer made by "SetupFactory". (SUF is short for SetUp Factory)
Trusted since 1991, Setup Factory is a rock-solid, reliable install creator for Windows applications
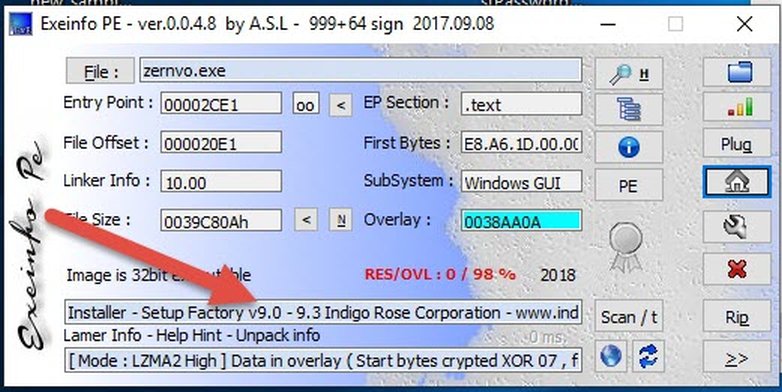
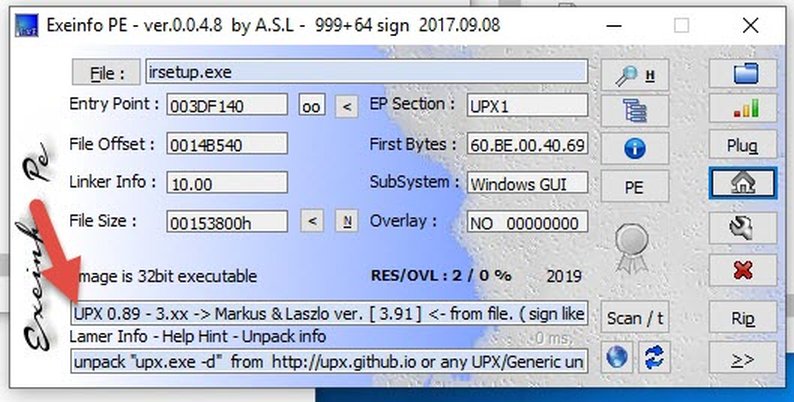
ExeinfoPE also confirms our findings:
At this point, the setup.exe was detected only by 16 / 70 AV engines on Virustotal, and most of them detect it as "Adware". And if we used an online automated malware scanner (hybrid-analysis or any.run), it will confirm that this executable does not download anything or try to modify your system maliciously.
So what does it do exactly?
.
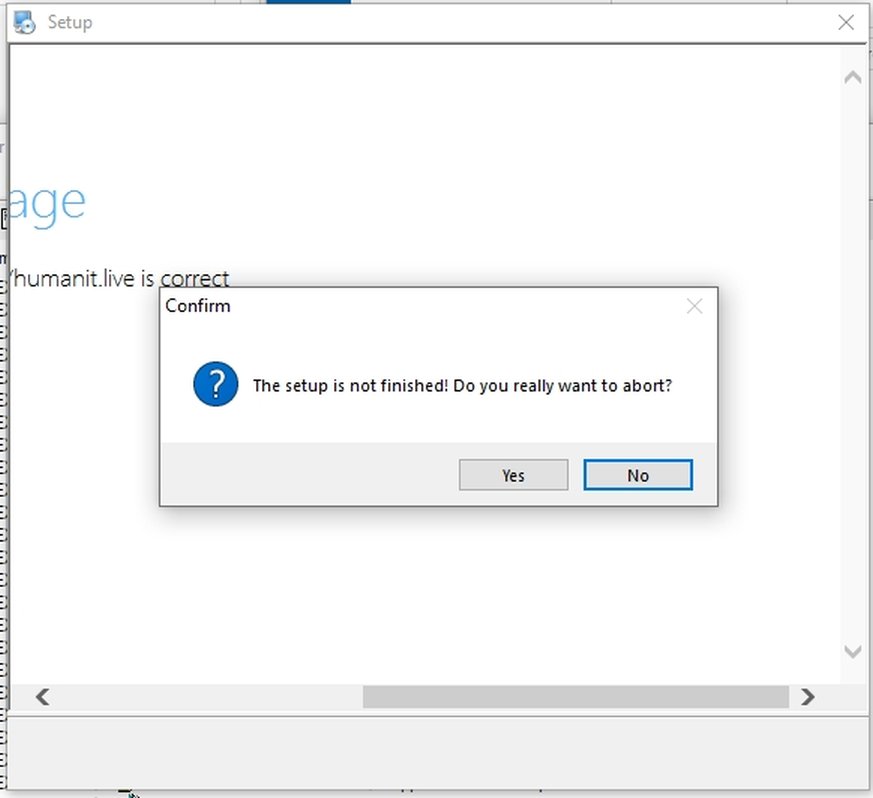
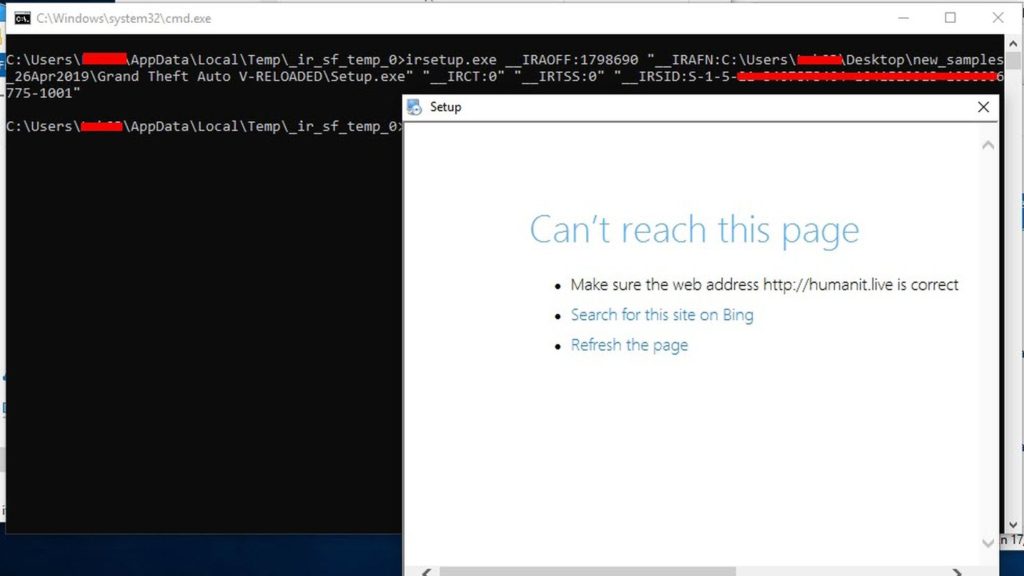
In order to find out, I disabled my internet connection and ran it, this showed up:
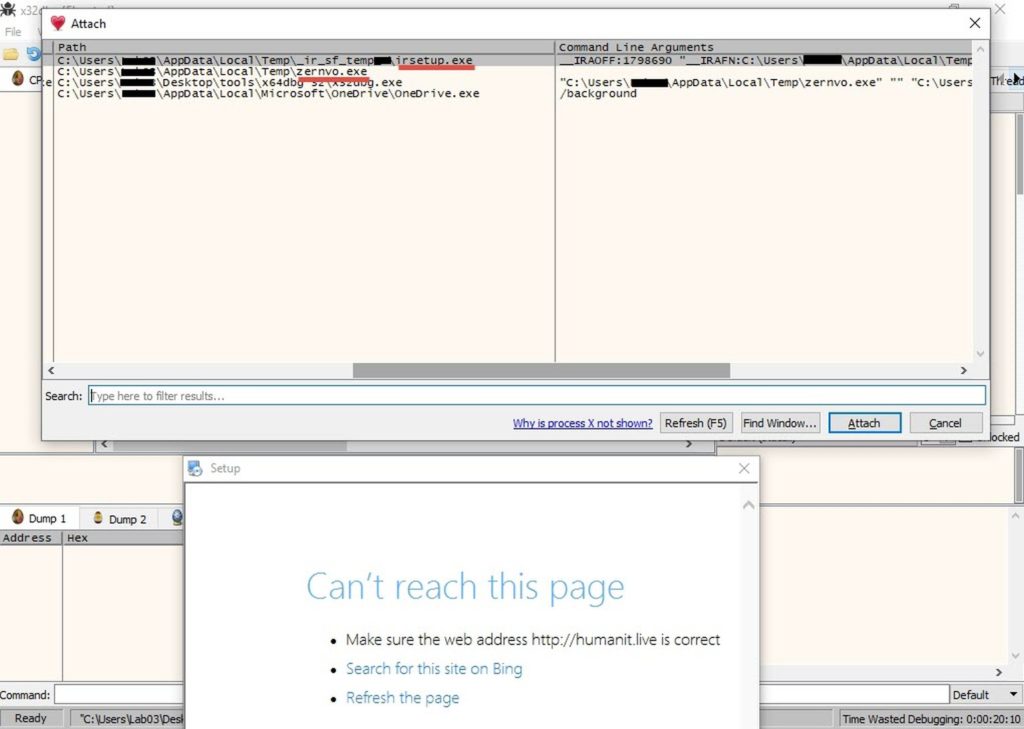
So it tries to connect to a website "hxxp://humanit.live". And if we try to close this window, it shows us a prompt (exactly like any legit installer). But we notice that there is no "next" button or anything that looks like a legit installer.
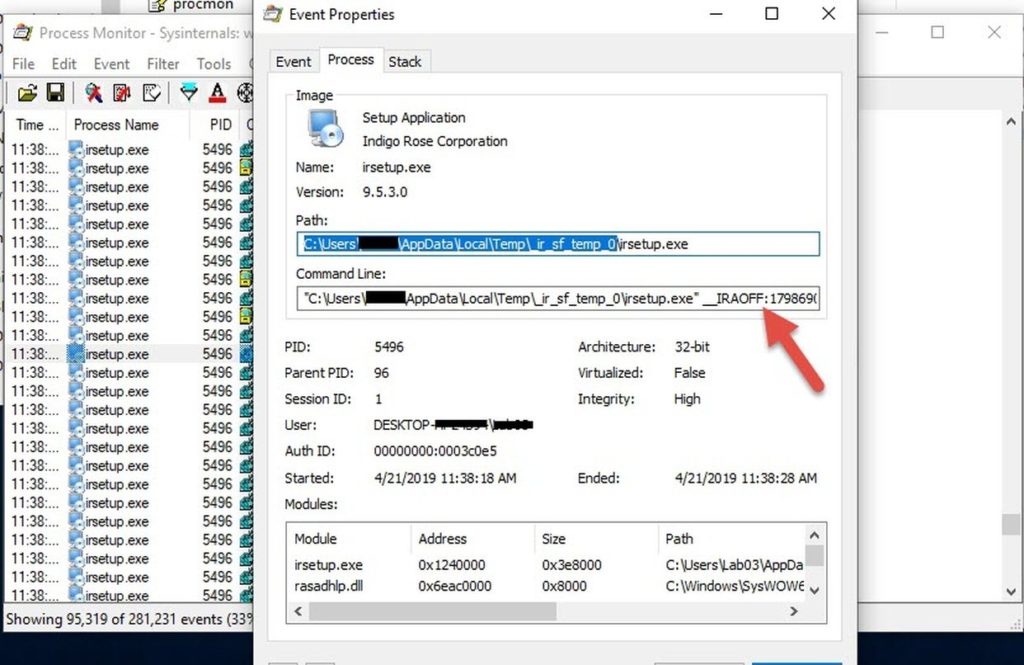
I had process monitor and process explorer running in the background, they showed that "setup.exe" unpacked into "%temp%\zernvo.exe", which in turn ran "irsetup.exe" with some parameters.
So we can conclude that"irsetup.exe" is the actual installer, and "setup.exe" was just a wrapper. (This is typical behaviour of any installer on windows).
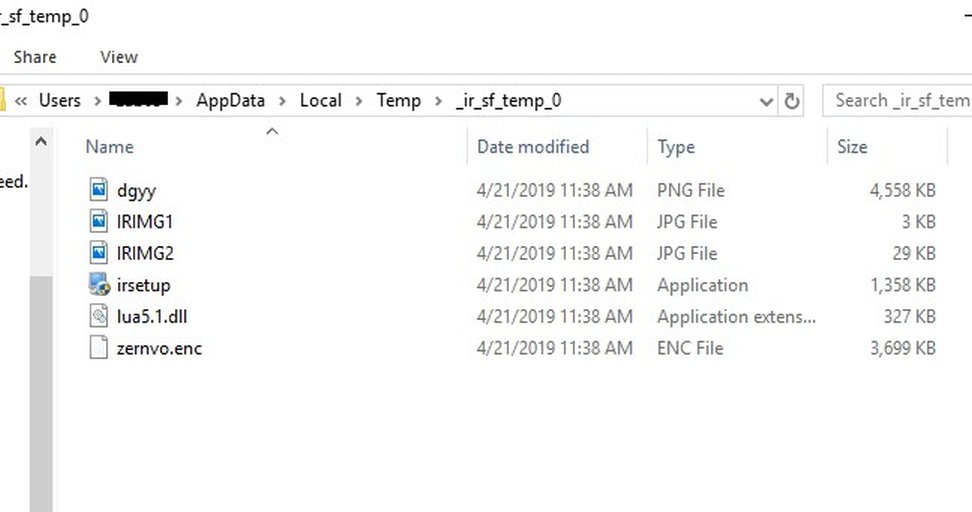
the temporary folder was this:
C:\Users\-redacted-\AppData\Local\Temp\_ir_sf_temp_0\
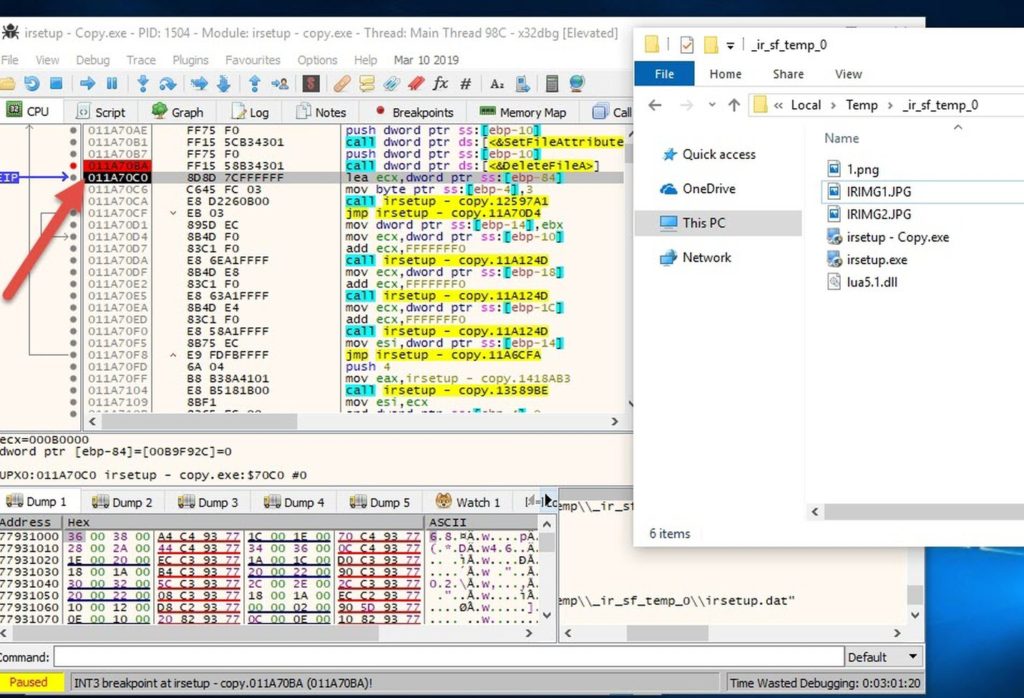
In that directory we find the following files:
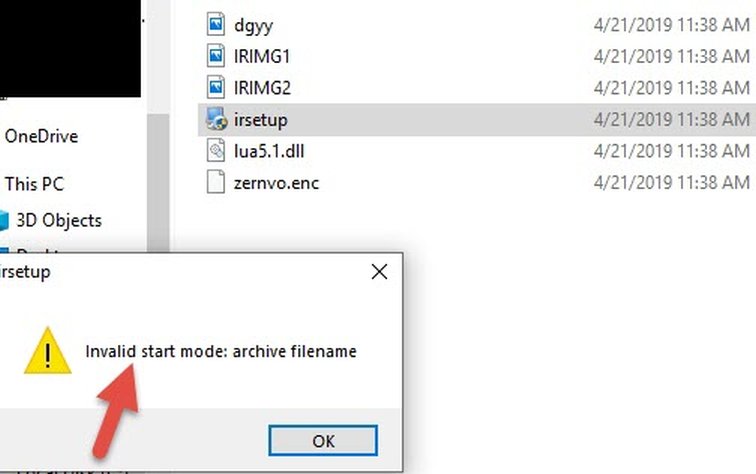
If we try to run irsetup.exe from this folder, we get an error message:
But if we run it with the same parameters we got from process monitor, it runs successfully.
irsetup.exe __IRAOFF:1798690 "__IRAFN:C:\Users\-redacted-\Desktop\new_samples_26Apr2019\Grand Theft Auto V-RELOADED\Setup.exe" "__IRCT:0" "__IRTSS:0" "__IRSID:S-1-5-21-redacted-"
Again, that is probably the normal behaviour of any SetupFactory installer. (I could dig deeper and reverse engineer Setup Factory to find out what each parameter does, but I decided not to do that once I knew that it is a legit installer)
.
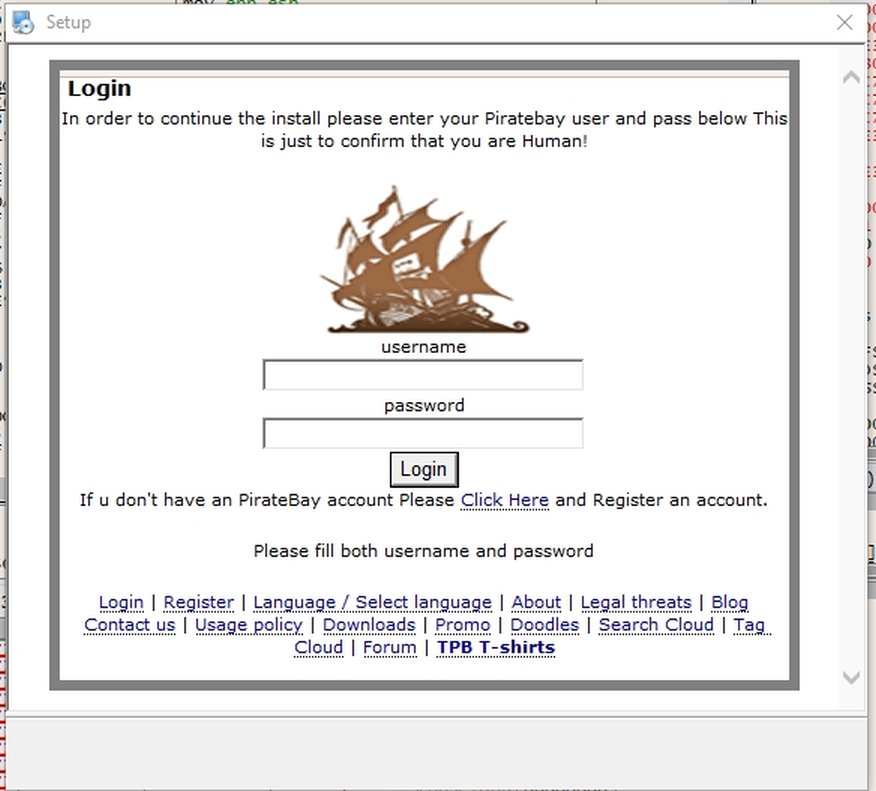
I ran it again after enabling the internet connection. It should now display the webpage at "hxxp://humanit.live".
Guess what?
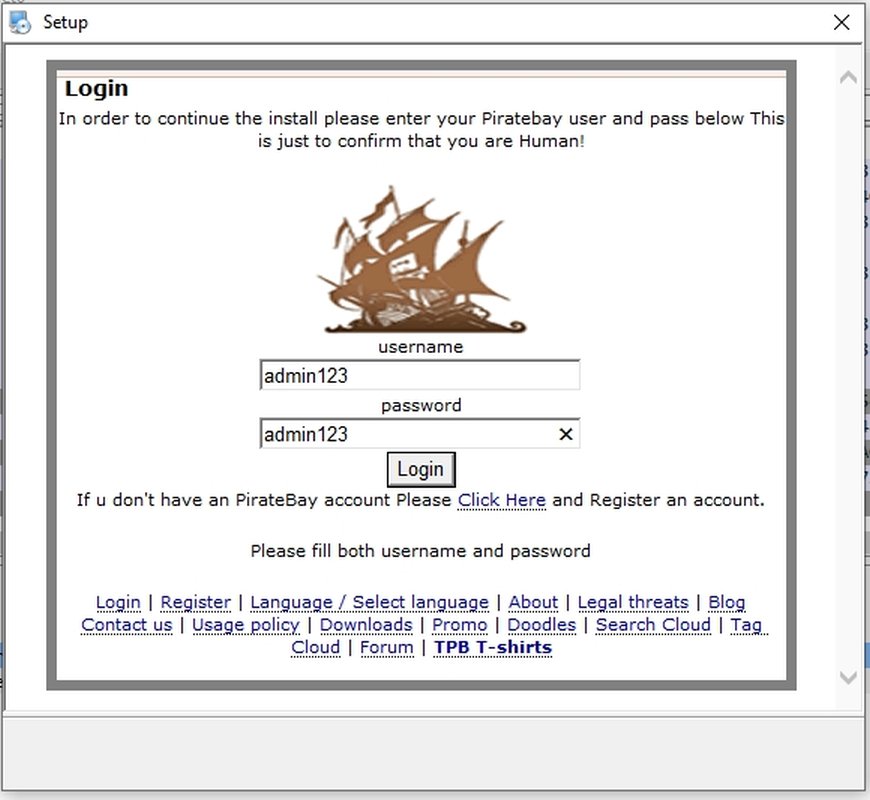
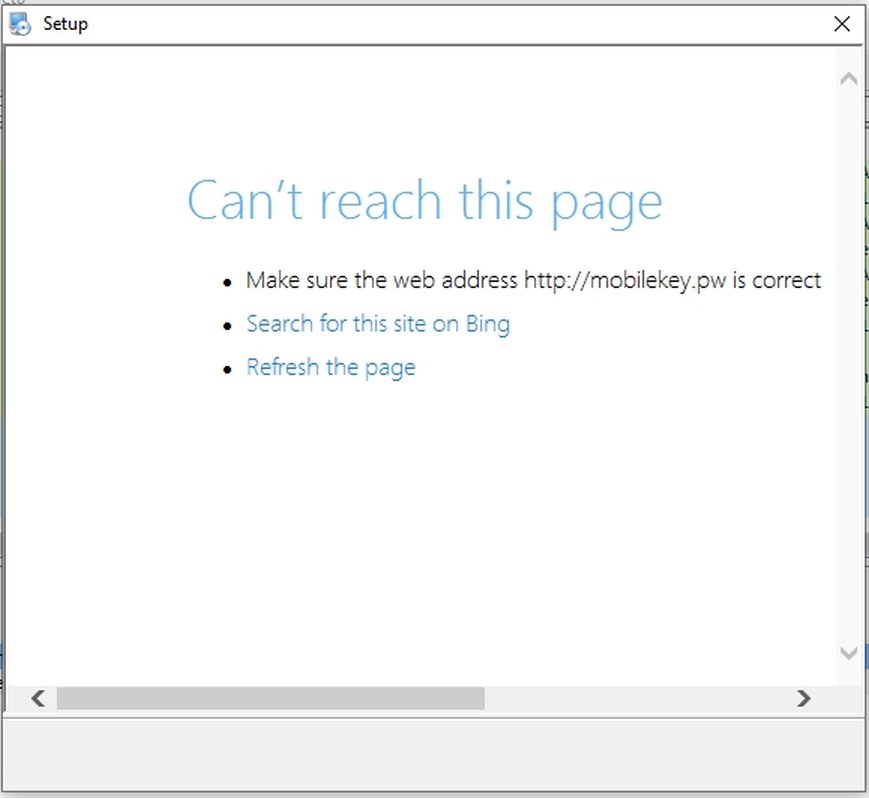
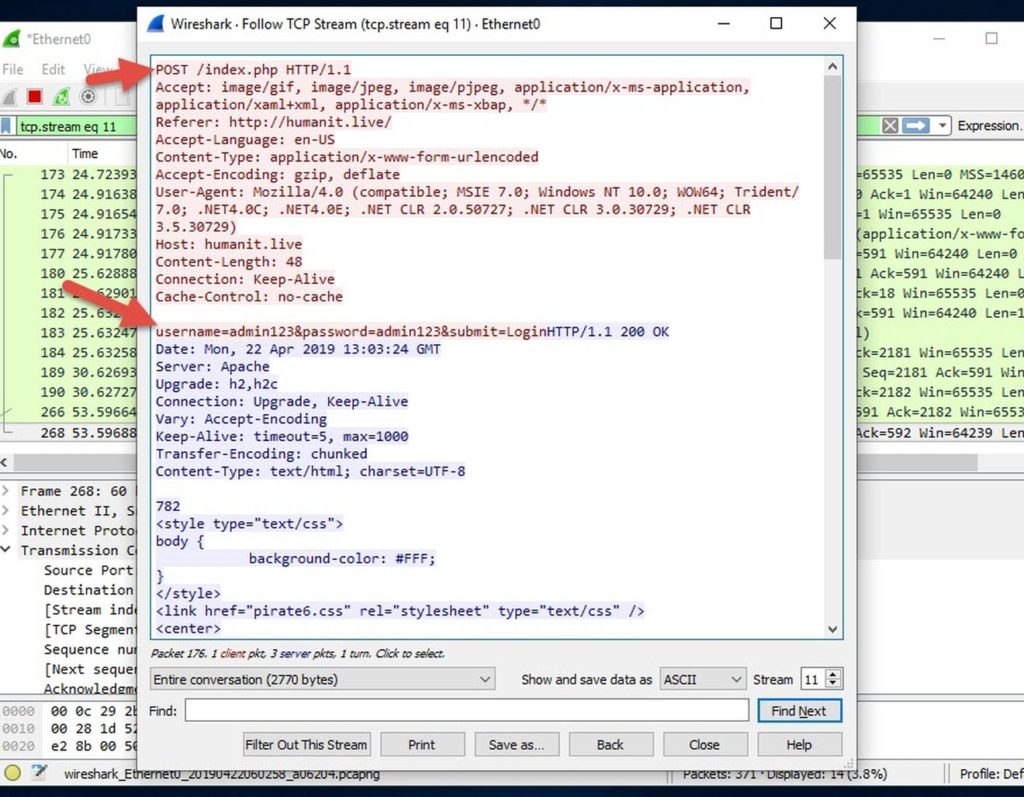
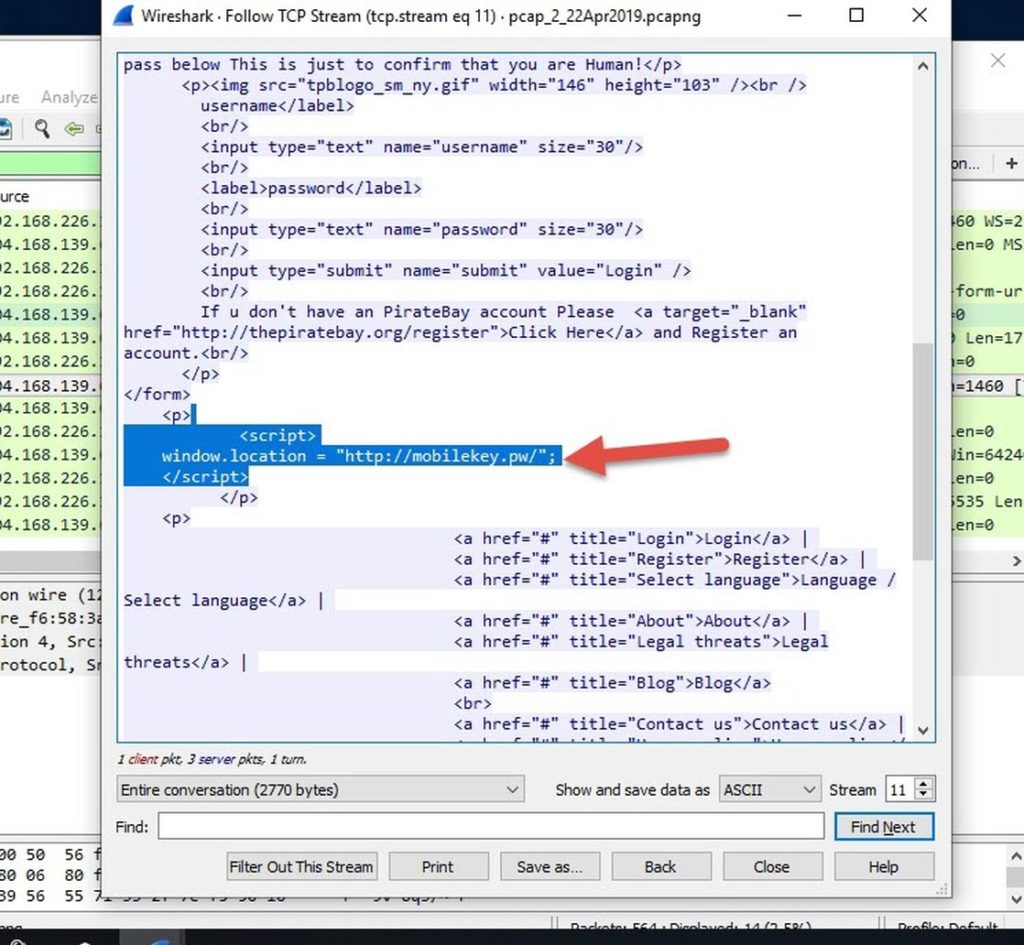
If I entered any fake credentials, it sends a POST-request to the same domain, then it redirects to another domain which is down now (hxxp://mobilekey.pw)
Sniffing the traffic with wireshark shows the details: (I have uploaded the PCAP file too if anyone wants to take a look).
If you entered a username and password in the POST request, it will insert a basic script in the page to redirect you to the second domain (hxxp://mobilekey.pw).
.
I wonder how will AntiViruses detect such malware? It's looks like a legit installer, but it contains a phishing URL in one of the steps of the setup.
I decided to research a bit into SetupFactory to know more.. and I found this thread on IndigoRose's forums:
when a setup is launched, several files are decompressed to the current \temp folder, just like the irsetup.dat file.
Unfortunately, exatcly that file holds all the information of a setup project. It can be viewed with a regular text editor, as it is not encrypted in any way.
I decided to hunt this "irsetup.dat" file. (by the way, the IR prefixes in this article probably stand for IndigoRose, the creator of Setup Factory).
I relooked at Process Monitor's logs, and I found that this file was indeed created by irsetup.exe and then deleted shortly after.
I could grab it using some software like CaptureBAT which will save a copy of the file before it is deleted. But I did it some other way...
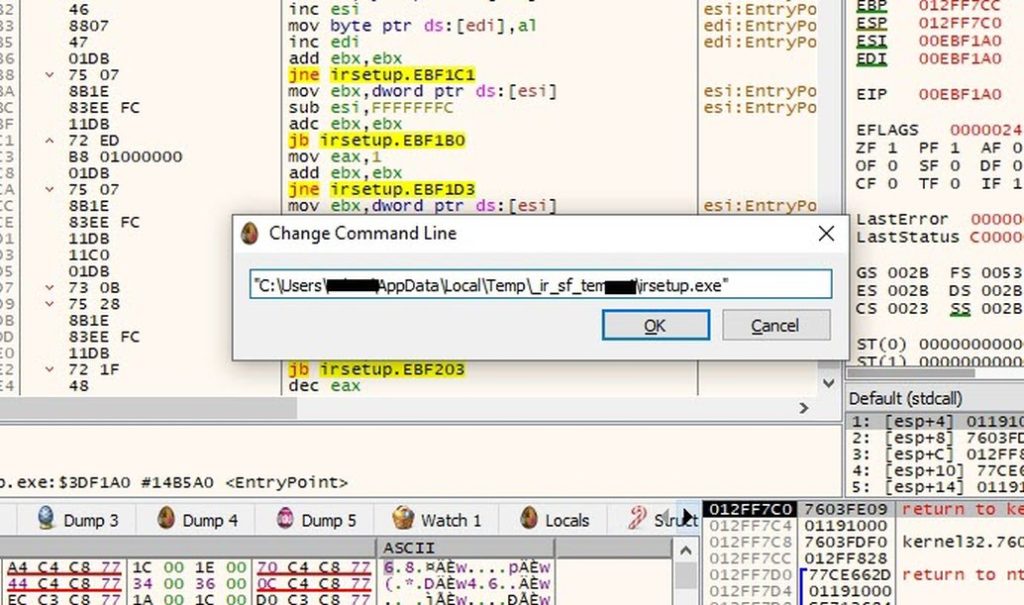
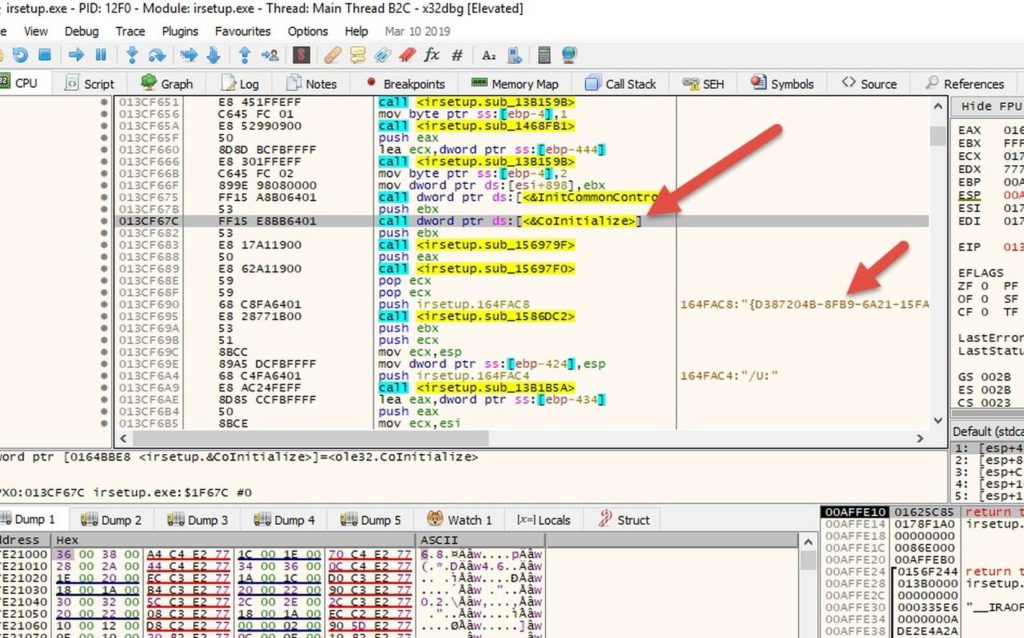
I attached to irsetup.exe using x32dbg, and ran it with the arguments I mentioned earlier.
I noticed that it's packed and it was starting the unpacking process (by reconstructing the imports table using LoadLibrary and GetProcAddress ). So I checked it in exeinfoPE, found that it's packed by UPX.
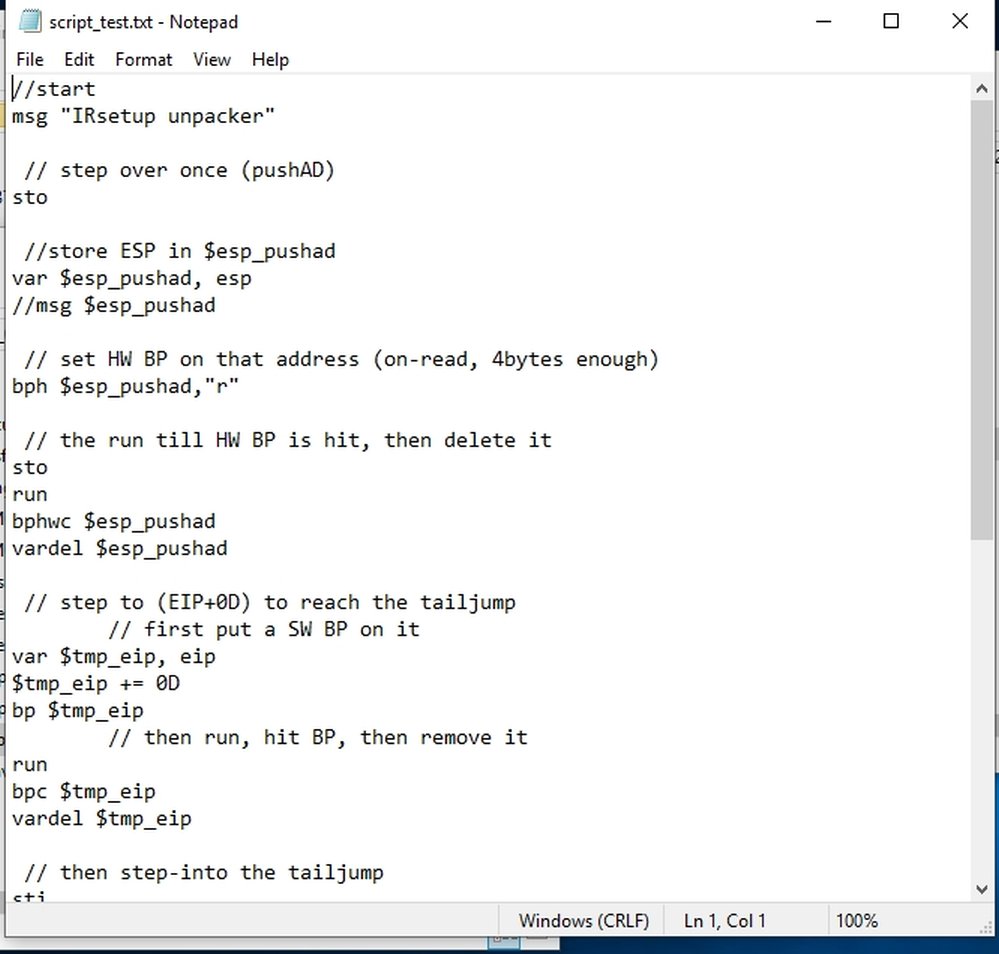
I created a simple script to skip the unpacking process (to speed up the debugging process).
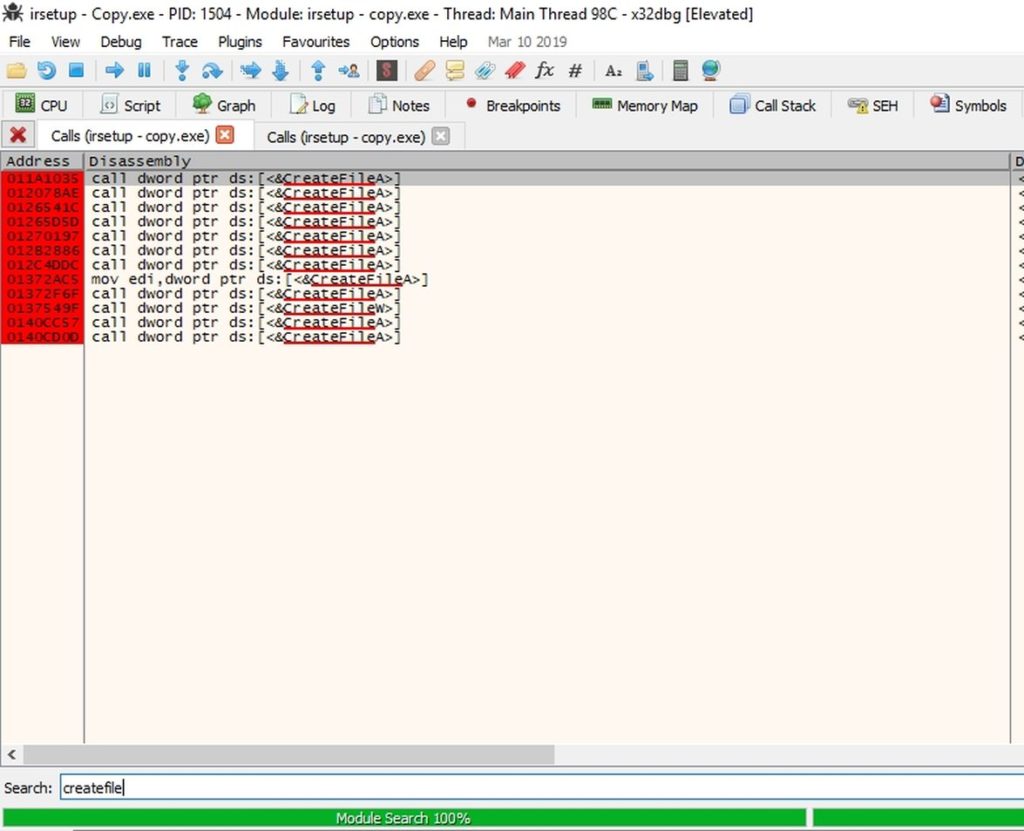
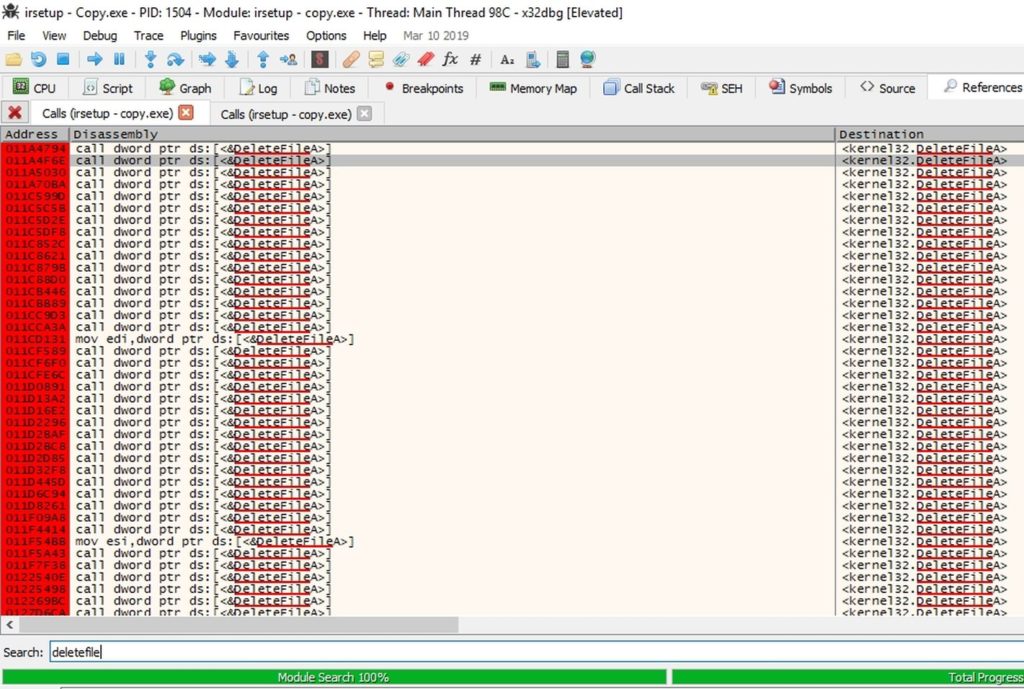
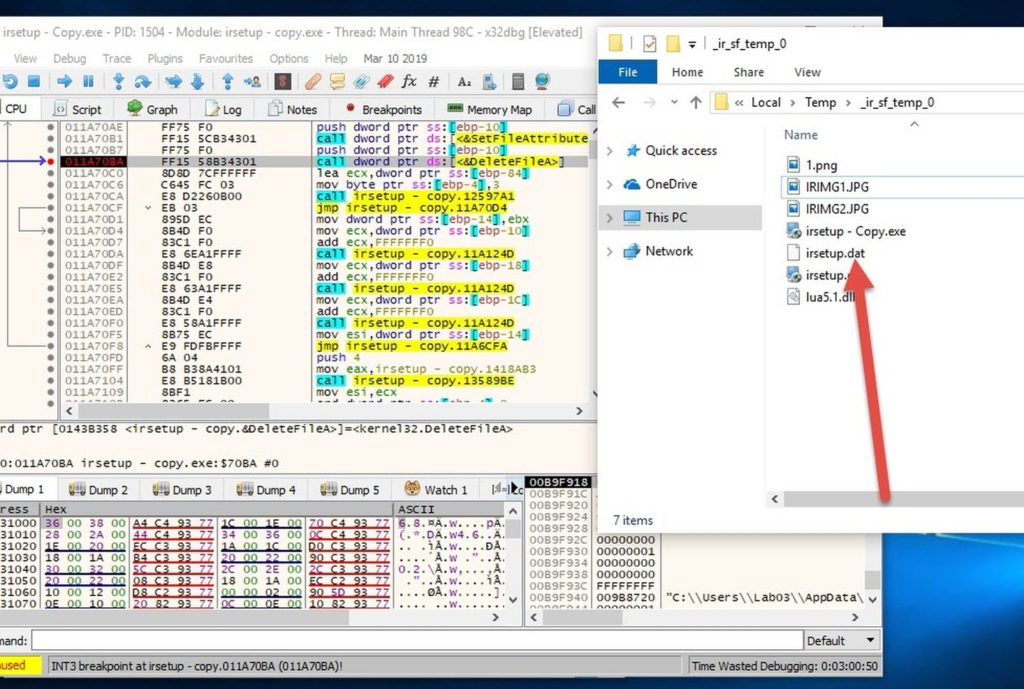
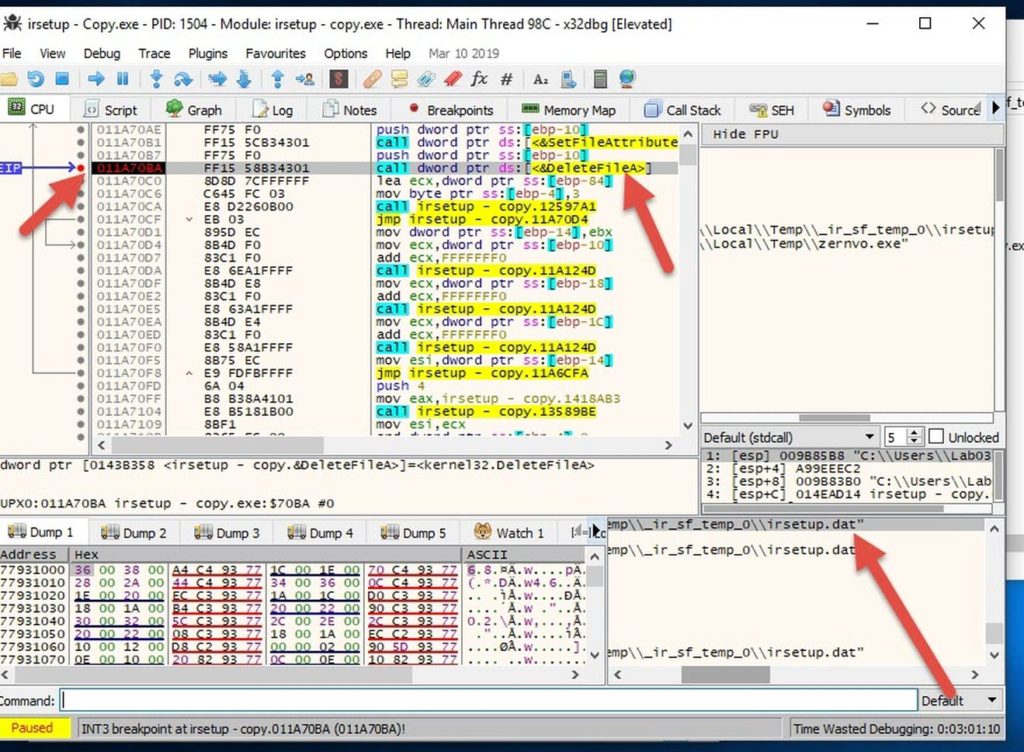
Then I put breakpoints on all calls to CreateFileA and DeleteFileA.
Then I kept running and hitting those breakpoints, until at one point the "irsetup.dat" file was created.
I copied it to a safe place, then I kept running until I found the deletion call.
Then I stepped over and the file was deleted..
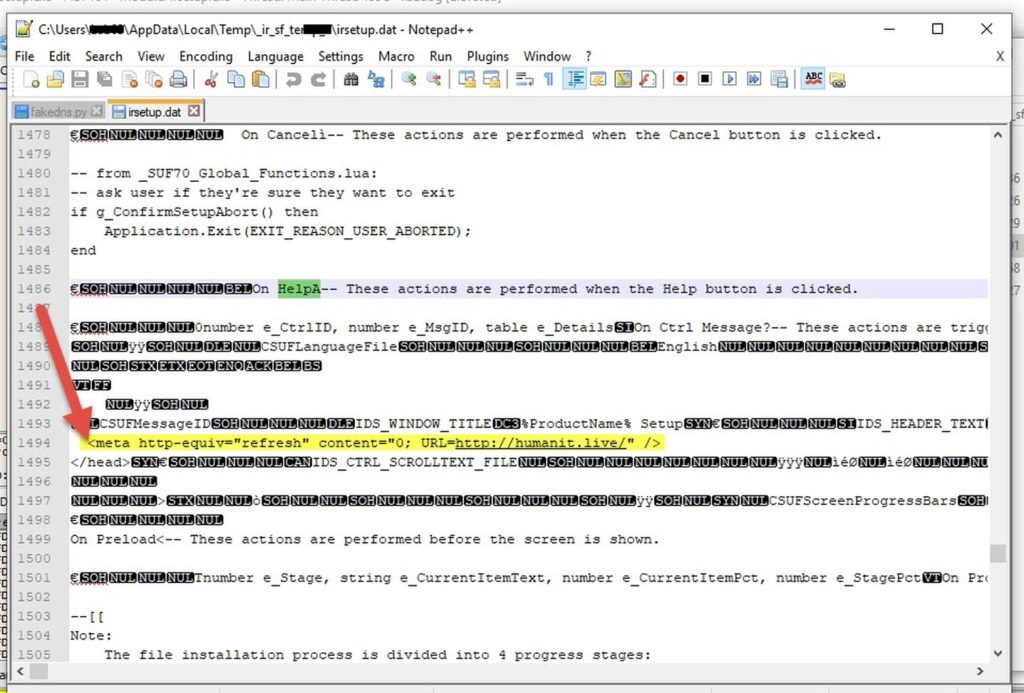
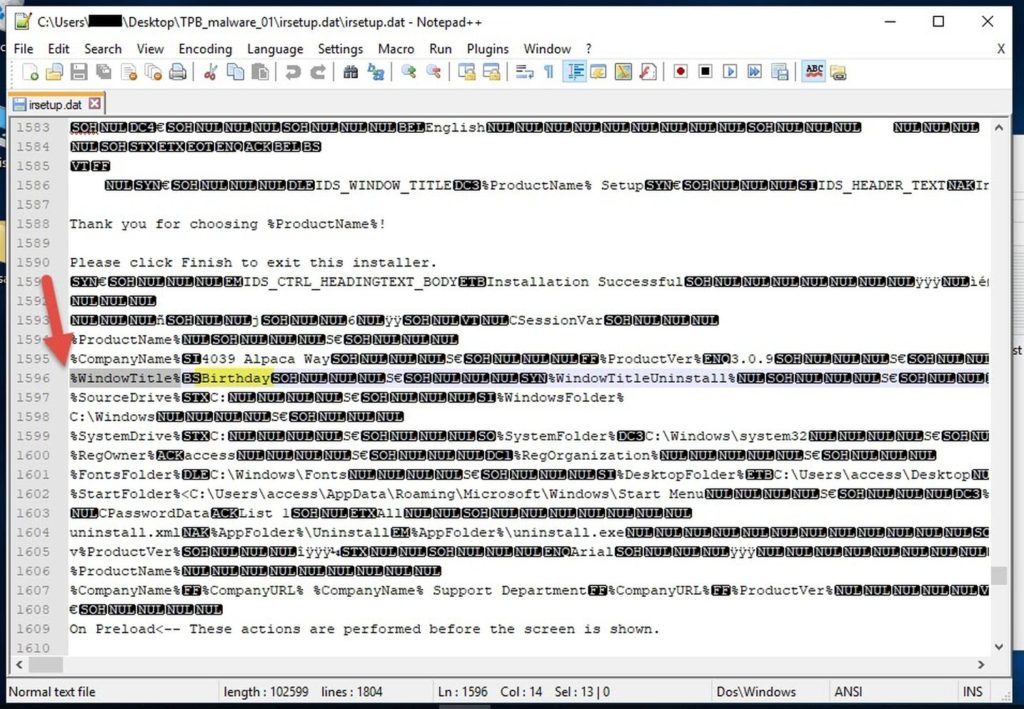
I opened "irsetup.dat" in a text editor. The file appeared to contain the setup's configuration.
This is the phishing URL..
Also the window title is called "Birthday"
.
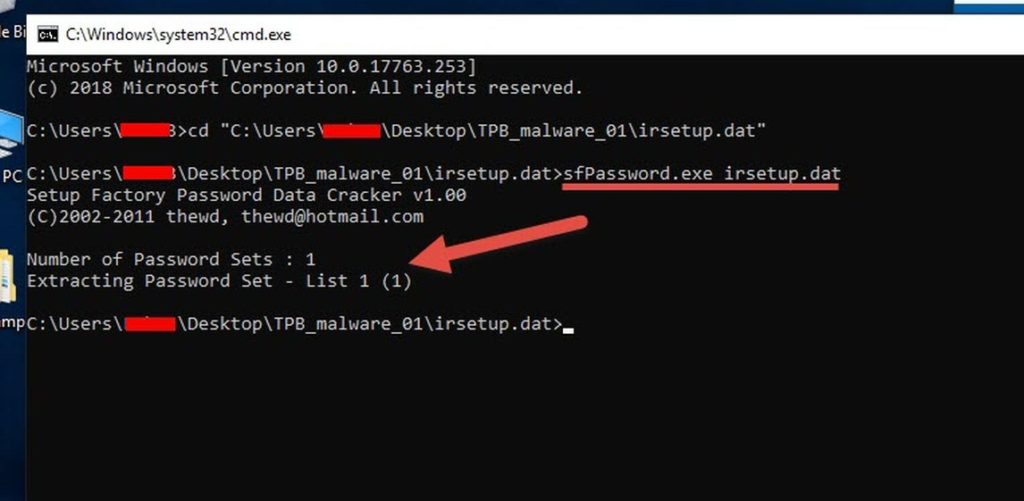
One more thing.. I googled "irsetup.dat" and found this on Github "Setup Factory Password Data Cracker".
Usage: sfPassword <setup configuration file>
<setup configuration file> : the setup configuration file which contains the password sets (irsetup.dat)
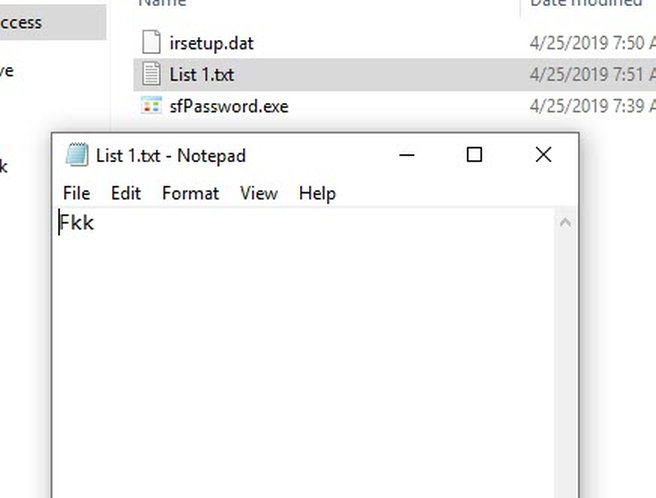
I ran it on our irsetup.dat and found this password:
I have no idea what to do with it. I think it may be used to unpack the setup.exe or something.. Please contact me if you understand what it does.
.
VirusTotal detections:
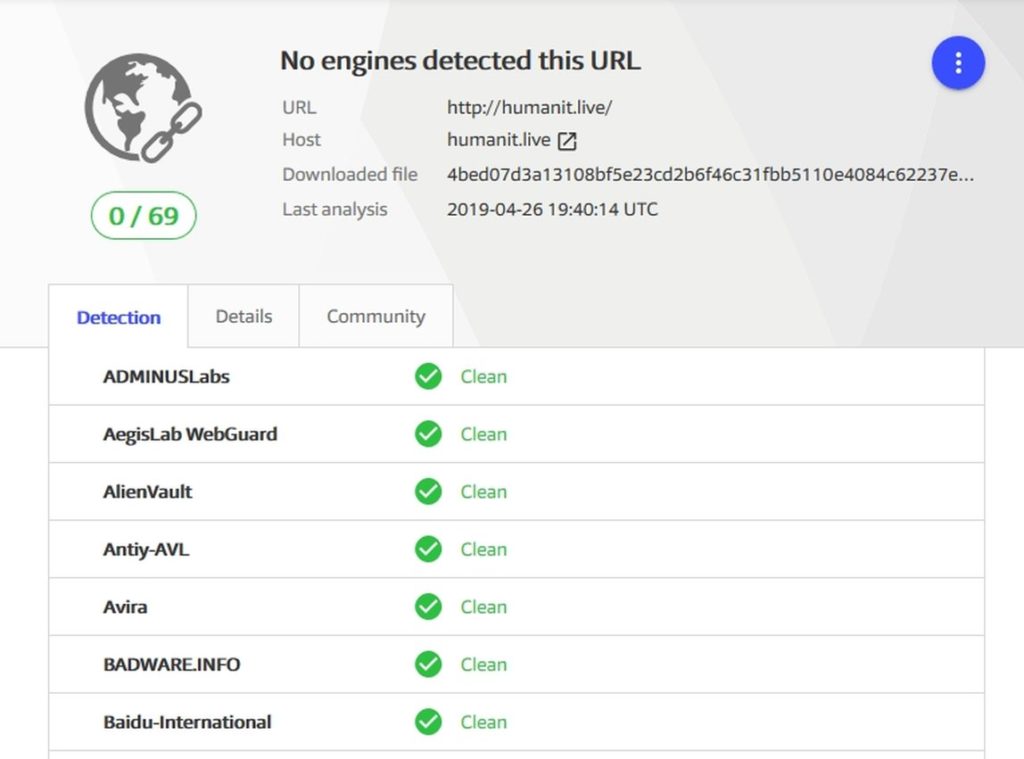
The strange thing is that Virustotal doesn't detect the phishing site as malicious. It says 0/66. Even till the time of this writing.
The "setup.exe" we grabbed from TPB has 17/71 detections.
"zernvo.exe" has 35/72 detections.
While "irsetup.exe" remains undetected (because it is the legit installer of Setup Factory), and it needs the irsetup.dat that contains the phishing link and stuff in order to behave maliciously. So it is not malicious on its own. We could see in this thread IndigoRose's forums that they had trouble before with AVs flagging their setups as malicious.
.
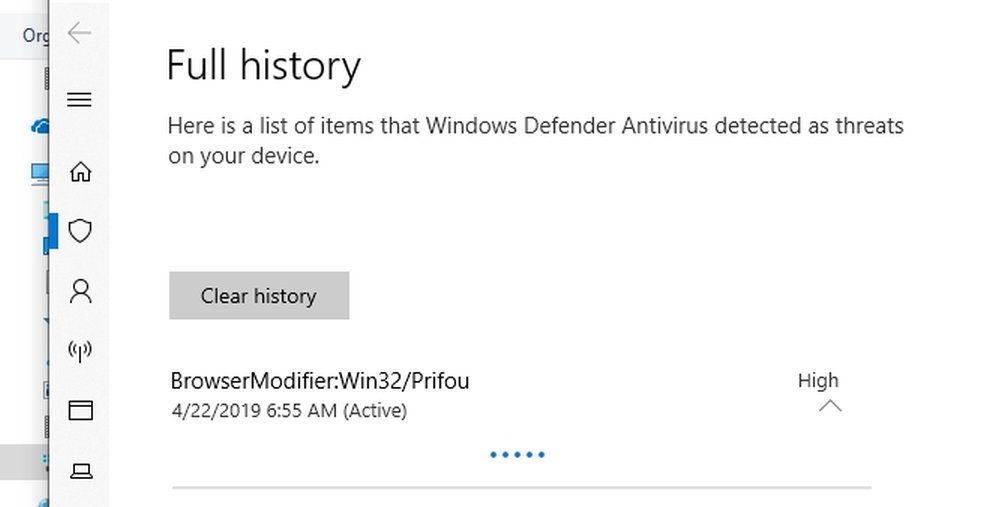
One interesting thing; after playing for an hour or so with "zernvo.exe", Windows Defender flagged it as "BrowserModifier:Win32/Prifou". And I had to get it back from the Quarantine. Good job Windows Defender ?
.
WhoIS on the domains:
WhoIS on the domains revealed that they were both registered at namecheap. No personal details were found.
humanit.live (using WhoisGuard of course) was created recently.
Updated Date: 2019-03-18T16:12:48Z
Creation Date: 2019-03-13T16:12:22Z
Registry Expiry Date: 2020-03-13T16:12:22Z
mobilekey.pw was created about a year ago, then it was renewed.
Updated Date: 2019-03-23T00:00:38.0Z
Creation Date: 2018-03-22T18:47:14.0Z
Registry Expiry Date: 2020-03-22T23:59:59.0Z
.
IOCs:
- humanit.live
- mobilekey.pw
- %temp%\zernvo.exe
I also found this GUID, but I think it's used by Setup Factory in general, not just by this piece of malware
- {D387204B-8FB9-6A21-15FA-0CD14BF40EA9}
.
Summary:
- A malware campaign is on ThePirateBay (TPB) torrent website disguising their malware as new PC games that you can download for free.
- All malwares are identical.
- The setup.exe files were created on 16-Apr-2019.
- It uses a setupFactory installer. and removes the "next" button and stuff from the setup, and instead puts a webpage to a phishing website. This way it could avoid detection by many AntiViruses.
- The phishing domain (hxxp://humanit.live) has 0 detections on VT. And it redirects you to another domain (hxxp://mobilekey.pw) which is down for now.
I've uploaded most files discussed in this article on github here.
Thanks to @macrovector for the free PNG vectors.
This is my first article on malware analysis, so feedback and criticism are very much appreciated.